AN ONGOING “MEOW” ATTACK DELETS THOUSANDS OF DATABASES
Thousands of unsecured internet-facing databases have been damaged and destroyed by the wave of attacks called “Meow”. After the attack is over, it leaves no explanation and no notes on what and why has happened, except for the only one word: Meow.
Meow-attacks started at the end of July 2020 and are still an ongoing issue, till now nearly 4000 DBs have been completely deleted, the majority are MongoDB and ElasticSearch but are not the only ones, also Cassandra, CouchDB, Redis, Hadoop, Jenkins, and Apache ZooKeeper have suffered Meow attacks.
Meow is an automated attack, it consists of a bot script that attacks a site by probing for known vulnerabilities such as unsecured ports and vulnerable files. Automated Meow attacks are targeting unsecured installations, for example, the ones without SSL encrypted communication, or the installations that are not protected by a firewall/WAF and are exposed to the public.
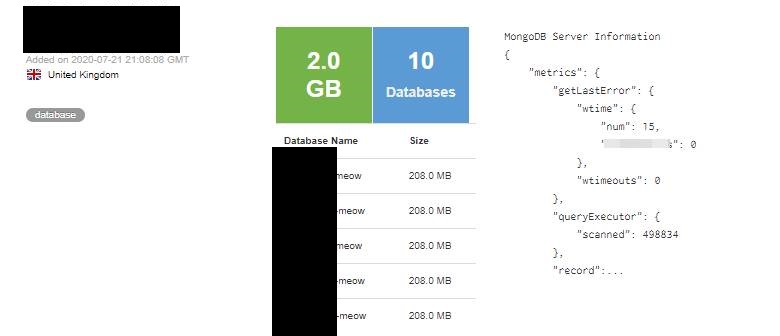
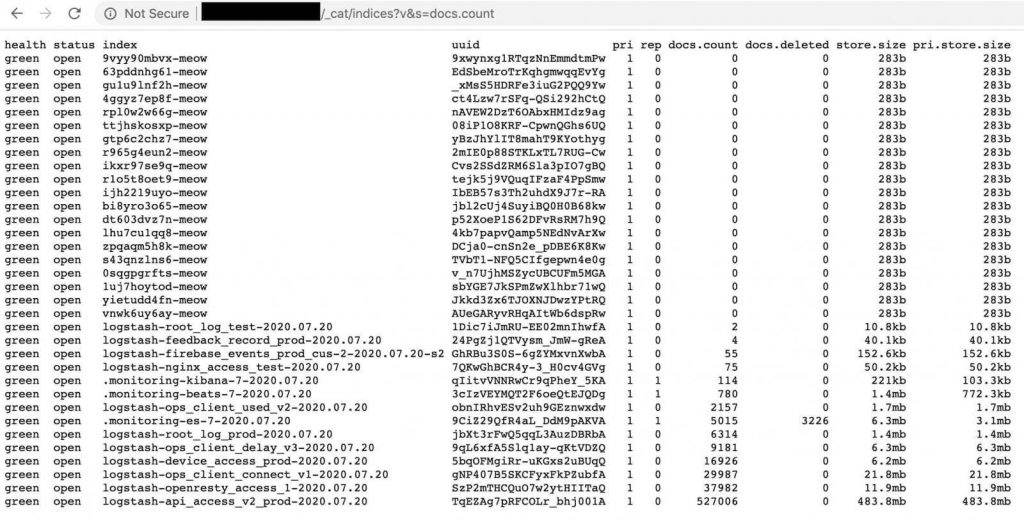
It is not quite clear what is the source and the motivation for Meow-hackers since such attacks do not have “global” menaces and do not contain any ransom threats, therefore malicious actors most probably are just doing it for fun, since hacking is becoming more accessible and easy year after year.
Bob Diachenko, a researcher and cybersecurity expert, was the first one to notice a strange wave of attacks that were taking advantage of the vulnerabilities the systems have. On his Twitter account, the researcher has presumed that most probably the hackers not only want to have fun but also want to teach a lesson and to make DB admins more sensible to IT security topics and pay more attention to securing the data.
However, even if the intentions may seem noble, the hackers have created serious damage to the companies. A huge Indian travel and online booking company have lost personal data of over 700.000 users, while a famous cosmetics brand Yves Rocher has lost millions of customer data.
How can you protect your data from Meow-like breaches?
1) Protect against script attacks – web sites rely heavily on scripts to run services and access data and the hackers always find a way to exploit those scripts to steal sensitive customer information. Malicious code can come from many sources, a solution that can detect script behavior will provide the most effective protection from these types of attacks.
Criticalcase in collaboration with Akamai Technologies implements Page Integrity Manager that takes a detection-first approach so that you can quickly mitigate compromised scripts and update policy controls to stop zero-day attacks and recurring attacks.
2) Use Multi-factor authentication (MFA) – today relying on just a username and password is no longer enough. The best solution is the one that can easily turn on MFA for any application with only one click — no development, testing, or maintenance required.
3) Assume all the data in your database is sensitive data and treat it accordingly. You need to know exactly where the data is and manage its security in an effective and easy way having control over the whole life cycle of the data.
4) Make sure key people in the company know who is responsible for database security.
5) Secure your data and apps with a WAF (Web Application Firewall), it inspects the traffic before it reaches your application and protects your server by filtering out threats that could damage your site or compromise data.
A WAF is an advanced solution that can protect you not only from any data BREACH but as well from SQL injection, Malicious file execution, Cross-site scripting, and more. A cloud-based WAF can scale to protect against the largest DoS and DDoS attacks. Criticalcase together with Akamai Technologies implements security solutions to eliminate any risks of downtime, data theft, and security breaches for its clients.
6) Work with a trusted technology partner that can provide you with a tailor-made and fully managed security solution.
Contact us
Fill out the form and one of our experts will contact you within 24 hours: we look forward to meeting you!


