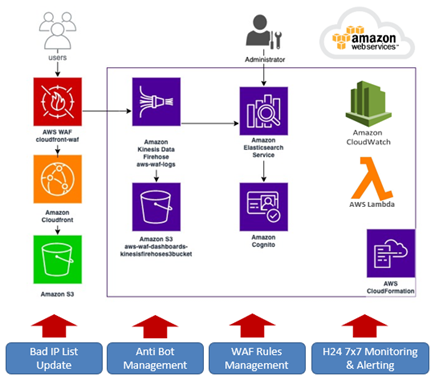
Another best practice I encourage you to follow is using a compression method. With AWS CloudFront, you can serve your applications using Brotli or GZip and dramatically reduce your content download speed.
Faster downloads, especially for JavaScript and CSS files, can result in faster rendering of your SPA.
Also, because CloudFront’s data transfer costs are based on the total amount of data served, managing compressed files is less expensive than managing uncompressed files.
Brotli is a widely used lossless compression algorithm that often outperforms Gzip in terms of compression ratio. Compared to Gzip, CloudFront’s Brotli edge compression results in files up to 24% smaller.
Compression capabilities can be enabled through the CloudFront console, SDK, and command line interface. EnableAcceptEncodingGzip must be set to true to return Gzip compressed objects and EnableAcceptEncodingBrotli to true to return Brotli compressed objects. CloudFront will use Brotli when the viewer supports both formats.
The Chrome and Firefox web browsers support Brotli compression only when the request is sent over HTTPS. Brotli is not supported with HTTP requests in these browsers.